Securing Internet Routing from the Ground Up

The Internet needs fixing
The Internet plays a crucial role in our daily lives, the global economy, national security, and beyond. Yet, the core components of the Internet’s communication infrastructure, which are tasked with routing data traffic, sharing the scarce network resources between users, and providing reliability in the face of attacks and failures, have remained fairly stagnant for decades. Consequently, the Internet is alarmingly vulnerable to attacks and fails to cope well with the constantly increasing performance requirements and the steeply rising number of users.
Deploying a new network technology (for routing, security, etc.) involves carefully engineering the technical solution, but also reasoning about the deployability of the solution and, in particular, about backwards compatibility with the existing infrastructure, incentives for early adopters, efficacy under partial adoption, and more. My research aims to devise practical, long-term solutions to the security-related and performance-related problems plaguing the Internet.
Internet routing is the Internet’s biggest security hole
Arguably, the Internet’s biggest security hole is the Border Gateway Protocol (BGP), which establishes routes between the tens of thousands of organisational networks that make up the Internet (e.g., Google, Facebook, Bank of England, Deutsche Telekom, AT&T). BGP stitches together these organisational networks and can thus be regarded as the glue that holds the Internet together. The insecurity of Internet’s routing system is constantly exploited to steal, monitor, and tamper with data traffic. Indeed, every year several high-profile attacks on the Internet routing system make the news while thousands of others go under the radar. However, despite over a decade of Herculean efforts, routing security remains a distant dream, leaving the Internet alarmingly insecure.
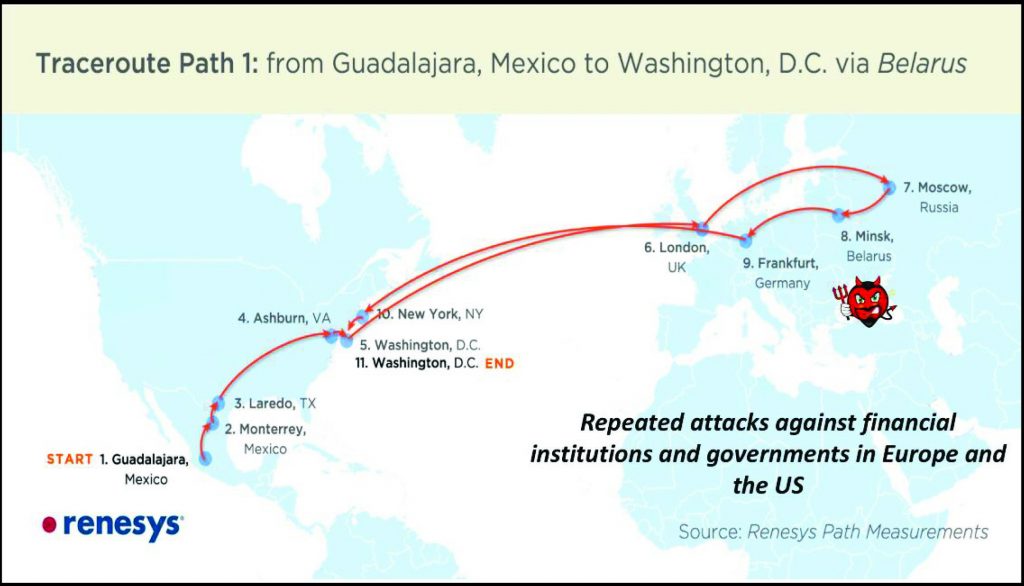
Internet traffic destined for Washington, D.C., re-routed through Belarus in November 2013 due to attacks on the Border Gateway Protocol
To illustrate just how vulnerable BGP is to attacks consider the particularly worrisome and common attack of “Internet-address hijacking”. Internet reachability to an organisation is established as information about how to reach Internet (i.e., IP) addresses owned by the organisation is propagated through the Internet using BGP. The process is initiated when BGP-speaking routers at the edge of the organisation advertise the Internet addresses belonging to the organisation to BGP-speaking routers at neighbouring organisations. This information is then propagated further via BGP to the neighbours’ neighbours, etc. Underlying BGP route-computation is thus the assumption of trust, i.e., that organisations disseminate via BGP their actual Internet addresses.
However, what’s to prevent a rogue organisation from advertising through BGP Internet addresses belonging to another organisation and thus attract traffic destined for the other organisation to its own network? The dismal answer is that essentially nothing is. Indeed, this occurs on a daily basis due to either configuration errors or targeted attacks. This type of attack, where an organisation advertises in BGP Internet addresses not belonging to it is effective and easy to launch, with the extra benefit of a plausible excuse: benign configuration errors (which are, sadly, prevalent).
Internet-address-hijacking attacks might be launched:
(1) to divert traffic destined for some organisation to somewhere else, thus effectively disconnecting the organisation from the Internet,
(2) to monitor and eavesdrop on traffic,
(3) to masquerade as another organisation (e.g., a bank, government body) by intercepting traffic to that organisation and responding to it,
(4) to conceal one’s own identity (e.g., by spammers) by sending traffic from hijacked Internet addresses that belong to others.
In fact as BGP underlies virtually all Inter-net services/applications, often attacks on such services (e.g., Blockchains, credit companies, etc.) are executed through attacks on BGP.
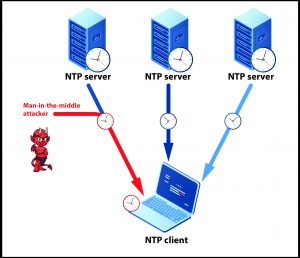
Using the Network Time Protocol (NTP), a computer system (e.g., smartphone, laptop, desktop) synchronizes time across over the Internet by issuing “time queries” to NTP servers and aggregating their responses to update its local time. NTP is highly vulnerable to “time shifting attacks” in which an attacker shifts the local time forward/backward by tampering with the communication to/from the NTP servers
Of course, the above is not new; the enormous threat that Internet-address-hijacking, and more sophisticated attacks on BGP, constitute, has been known for at least a decade. Moreover, the Internet Engineering Task Force (IETF) has been promoting solutions for this issue for a long while. However, the adoption of these solutions is discouragingly slow for technological, political, and economic reasons (5,7), leaving the vast majority of the Internet completely vulnerable to disastrous attacks.
The SIREN ERC-funded project
I argue that the reasons for this are deeply rooted in today’s centralised, top-down, hierarchical paradigm for securing Internet routing. The aim of the SIREN ERC-funded research project is to put forth and explore a radically new paradigm for securing routing on the Internet. The proposed alternative roadmap for securing the Internet consists of exploring two complementary directions:
Jumpstarting BGP security – I aim to devise security solutions that are readily deployable in the sense that they do not require modifying/replacing today’s BGP routing infrastructure (e.g., BGP routers), can be deployed by an organisation with-out any coordination with others, provide tangible benefits even for very early adopters, and enhance security even under very partial deployment. We report on first steps in this direction in (3,6,8).
A long-term vision for Internet routing – Alongside the above direction for improving BGP security in the near/ medium-term, the SIREN project also investigates the following long-term agenda. The root cause for BGP’s insecurity is that route-computation is decentralised across self-interested, error-prone, and sometimes even malicious parties. Can the vast computational resources in modern-day datacentres, and recent advances in privacy-preserving computation, be leveraged to outsource routing to a small number of entities while retaining flexibility, autonomy and privacy? See (1,2) for some results along these lines.
BGP is not alone: securing network time
Other crucial components of the Internet’s communication infrastructure, designed and deployed in the same era (e.g., the Domain Name System, the TCP/IP protocol suite) suffer from similar drawbacks. An important and timely illustration is the Network Time Protocol (NTP), which synchronises time across computer systems over the Internet. NTP is highly vulnerable to attacks that shift the local time at a computer system forward/backward. Such attacks have recently been shown to seriously under-mine the correctness and security of crucial Internet applications/protocols. As part of the SIREN project my research group at Hebrew University is also investigating how the security of other core Internet protocols, including NTP, can be enhanced. See (4) and also the exposition of our results at this link.
Our results for both BGP security and NTP security have been awarded the IETF/IRTF Applied Networking Research Prize, awarded for recent results in applied networking research that are relevant for transitioning into shipping Internet products and related standardization efforts.
References:
1 Gilad Asharov, Daniel Demmler, Michael Schapira, Thomas Schneider, Gil Segev, Scott Shenker, Michael Zohner: Privacy-Preserving Interdomain Routing at Internet Scale. PoPETs 2017(3): 147 (2017)
2 Marco Chiesa, Daniel Demmler, Marco Canini, Michael Schapira, Thomas Schneider: SIXPACK: Securing Internet eXchange PointsAgainst Curious onlooKers.CoNEXT2017:120-133
3 AvichaiCohen,YossiGilad,AmirHerzberg,Michael Schapira:JumpstartingBGPSecuritywithPath-End Validation.SIGCOMM2016:342-355
4 Omer Deutsch, Neta Rozen Schiff, Danny Dolev, MichaelSchapira:Preventing(Network)TimeTravel withChronos.NDSS2018
5 YossiGilad,AvichaiCohen,AmirHerzberg,Michael Schapira, Haya Shulman: Are We There Yet? On RPKI’sDeploymentandSecurity. NDSS2017
6 YossiGilad,TomasHlavacek,AmirHerzberg,Michael Schapira, and Haya Shulman: Perfect is the Enemy of Good: Setting Realistic Goals for BGP Security. HotNets18
7 Robert Lychev, Sharon Goldberg, Michael Schapira: BGP security in partial deployment: is the juice worththesqueeze?SIGCOMM2013:171-182
8 Robert Lychev, Michael Schapira, Sharon Goldberg: Rethinking security for internet routing. Commun. ACM59(10):48-57(2016)


